The threat actor behind the Fodcha distributed denial-of-service (DDoS) botnet has resurfaced with new capabilities, researchers reveal.
This includes changes to its communication protocol and the ability to extort cryptocurrency payments in exchange for stopping the DDoS attack against a target, Qihoo 360’s Network Security Research Lab said in a report published last week.
Fodcha first came to light earlier this April, with the malware propagating through known vulnerabilities in Android and IoT devices as well as weak Telnet or SSH passwords.
The cybersecurity company said that Fodcha has evolved into a large-scale botnet with over 60,000 active nodes and 40 command-and-control (C2) domains that can “easily generate more than 1 Tbps traffic.”
Peak activity is said to have occurred on October 11, 2022, when the malware targeted 1,396 devices in a single day.
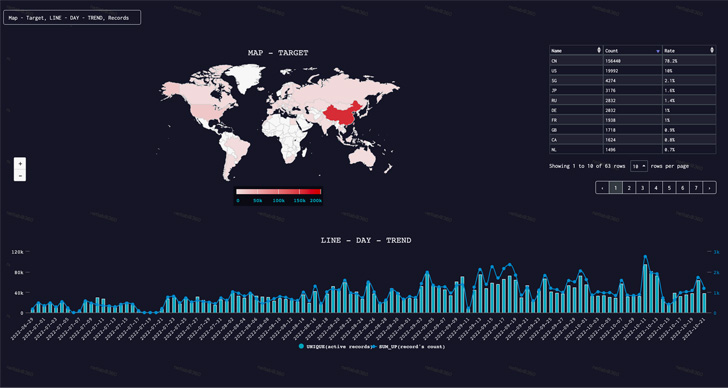
The top countries singled out by the botnet since late June 2022 comprises China, the U.S., Singapore, Japan, Russia, Germany, France, the U.K., Canada, and the Netherlands.
Some of the prominent targets range from healthcare organizations and law enforcement agencies to a well-known cloud service provider that was assaulted with traffic exceeding 1 Tbps.
Fodcha’s evolution has also been accompanied by new stealth features that encrypt communications with the C2 server and embed ransom demands, making it a more potent threat.
“Fodcha reuses a lot of Mirai’s attack code, and supports a total of 17 attack methods,” the cybersecurity company noted.
The findings come as new research from Lumen Black Lotus Labs pointed out the growing abuse of the Connectionless Lightweight Directory Access Protocol (CLDAP) to magnify the scale of DDoS attacks.
To that end, as many as 12,142 open CLDAP reflectors have been identified, most of which are distributed in the U.S. and Brazil, and to a lesser extent in Germany, India, and Mexico.
In one instance, a CLDAP service associated with an unnamed regional retail business in North America has been observed directing “problematic amounts of traffic” towards a wide range of targets for more than nine months, emitting up to 7.8 Gbps of CLDAP traffic.
The Black Lotus Labs warning also coincides with a joint advisory released by U.S. government agencies to help organizations take proactive steps to reduce the likelihood and impact of DDoS attacks.
As preventive measures, enterprises are urged to identify critical assets, understand how users connect to the corporate networks, enroll in a DDoS protection service, and develop DDoS response and business continuity plans.
“IoT devices are internet-connected and often use default passwords and lack sound security postures, making them vulnerable to compromise and exploitation,” the U.S. Cybersecurity and Infrastructure Security Agency (CISA) said.
“Because infections of IoT devices often go unnoticed by users, an attacker could easily assemble hundreds of thousands of these devices into a formidable botnet capable of conducting a high-volume attack.”